Recommended Services
Supported Scripts
Managed Firewalls
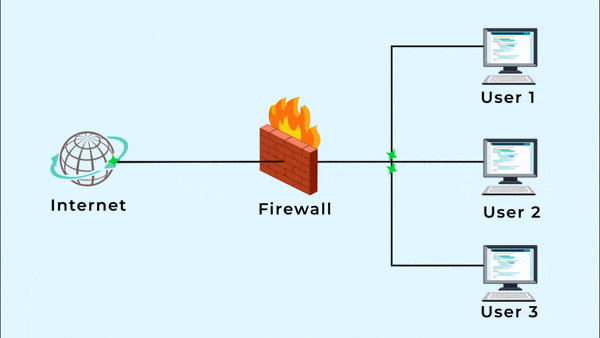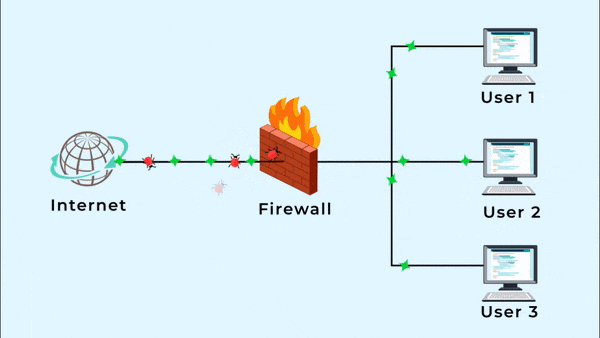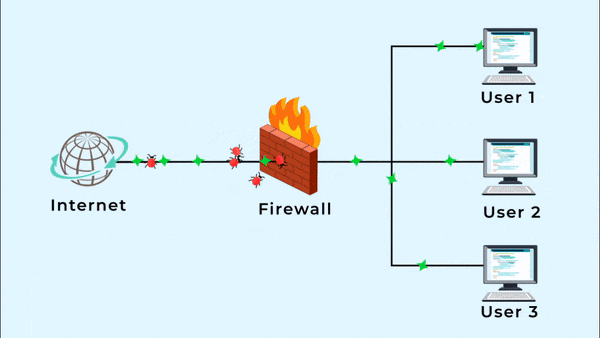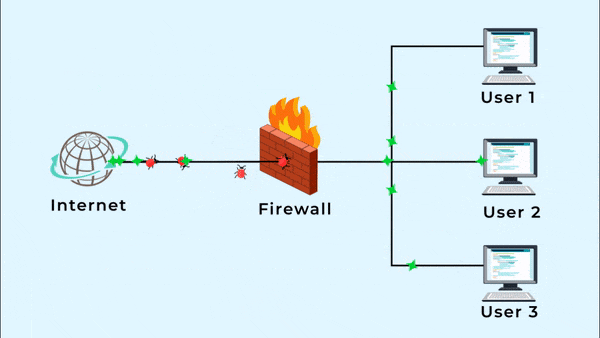
Protect Your Network
IAMEM's Advanced Managed Firewalls Redefining Security and Productivity
IAMEM’s Managed Firewalls service goes beyond the traditional scope of a firewall—offering secure access, enhanced visibility, and comprehensive control to empower your business with stronger cybersecurity and improved productivity.
Our Managed Firewall Solution
the cost of a security analyst.
network outages or crippling cyberattacks
Protect Your Network Effectively for Less with Managed Firewalls from IAMEM
Managing your network in-house can be time-consuming and costly. IAMEM’s Managed Firewall service delivers enterprise-grade protection at a fraction of the cost of hiring an in-house security analyst. Our team is available 24/7/365 to secure your network through expert administration, operation, monitoring, and maintenance of your firewall.

IAMEM's Managed Firewall solution includes Intrusion Detection (IDS) and Prevention (IPS) systems to detect and block cyber threats. IDS alerts you to suspicious activity, while IPS prevents malicious packets from entering your network.
IAMEM's Managed Firewall uses gateway anti-virus to block
malware hidden in web traffic. It scans HTTP, HTTPS, SMTP,
and FTP traffic for malicious code and prevents access
to infected sites.
IAMEM's firewall management services provide visibility into network activity, from top applications to VPN users. Web content filtering enforces company policies by blocking unauthorized browsing.
IAMEM's Managed Detection and Response (MDR) enhances firewall controls with expert analysts and advanced technology to detect hidden threats and deliver swift, coordinated responses.
- Threat Detection: Are you identifying potential threats in real-time?
- Access Control: Do you have strict protocols for who can access your network?
- Firewall Protection: Is your firewall updated and configured to block emerging threats?
- Data Encryption: Are sensitive data transmissions adequately encrypted?
- Security Audits: How often do you perform comprehensive network security audits?
- Endpoint Protection: Are all devices connected to your network secure and monitored?
- Compliance Standards: Does your network meet industry regulations like HIPAA or PCI DSS?
- Incident Response: Do you have a rapid response plan for security breaches?
- Monitoring Tools: Are you using 24/7 monitoring tools to oversee network activity?
- Employee Training: Are employees aware of security best practices to prevent breaches?
- Open Ports: Leaving unnecessary ports open can expose your network to unauthorized access.
- Weak Access Control Rules: Using overly permissive rules that allow too much traffic can compromise security.
- Lack of Regular Updates: Failing to regularly update firewall software leaves it vulnerable to known exploits.
- Improper Logging: Not enabling logging or storing logs improperly can hinder threat detection and forensic analysis.
- Misconfigured VPN Settings: Allowing insecure or poorly configured VPN connections can provide an entry point for attackers.
- Failure to Block Unused Protocols: Leaving unnecessary protocols (like ICMP or Telnet) open can give attackers potential vectors for exploitation.
Technologies we work with




Contact Us For an Evaluation
Frequently Asked Questions FAQs
A firewall is your first line of defense. It is a network security device that monitors incoming and outgoing traffic, deciding whether to allow or block specific traffic based on predefined security policies and rules. This can include restricting access to certain applications or websites, blocking malicious traffic, and preventing unauthorized access to sensitive data. To learn more about how a managed firewall works, contact IAMEM.
Yes, it definitely does. With cyber threats becoming more sophisticated, a firewall is a vital part of any comprehensive network security strategy. IAMEM’s firewall helps protect your company from a wide range of cyber threats, including viruses, malware, and unauthorized access. By filtering network traffic based on predefined security policies, it ensures that only legitimate traffic enters your network, reducing the risk of a successful cyberattack.
Configuring the firewall involves setting up rules and policies to control network access, as well as configuring settings like logging and reporting. Once deployed and configured, the firewall must be continuously monitored and managed to ensure its effectiveness in detecting and addressing potential cyber threats. Since this can be time-consuming and complex, many businesses choose a managed firewall service. With IAMEM’s managed firewall service, we handle everything—from deployment and proper configuration to ongoing 24/7 management.
While in-house solutions can take years and thousands of dollars to fully develop, IAMEM’s complete managed firewall service can be deployed quickly, providing immediate value to your business.

